This project implements the research from the paper “Careless Whisper: Exploiting Silent Delivery Receipts to Monitor Users on Mobile Instant Messengers” by Gabriel K. Gegenhuber, Maximilian Günther, Markus Maier, Aljosha Judmayer, Florian Holzbauer, Philipp É. Frenzel, and Johanna Ullrich (University of Vienna & SBA Research).
What it does: By measuring Round-Trip Time (RTT) of WhatsApp message delivery receipts, this tool can detect:
- When a user is actively using their device (low RTT)
- When the device is in standby/idle mode (higher RTT)
- Potential location changes (mobile data vs. WiFi)
- Activity patterns over time
Security implications: This demonstrates a significant privacy vulnerability in messaging apps that can be exploited for surveillance.
⚠️ DISCLAIMER: The tool is for educational and security research purposes only. Demonstrates privacy vulnerabilities in WhatsApp and Signal.
Installation
# Clone repository git clone https://github.com/gommzystudio/device-activity-tracker.git cd device-activity-tracker # Install dependencies npm install cd client && npm install && cd ..
Requirements: Node.js 20+, npm, WhatsApp account
Usage
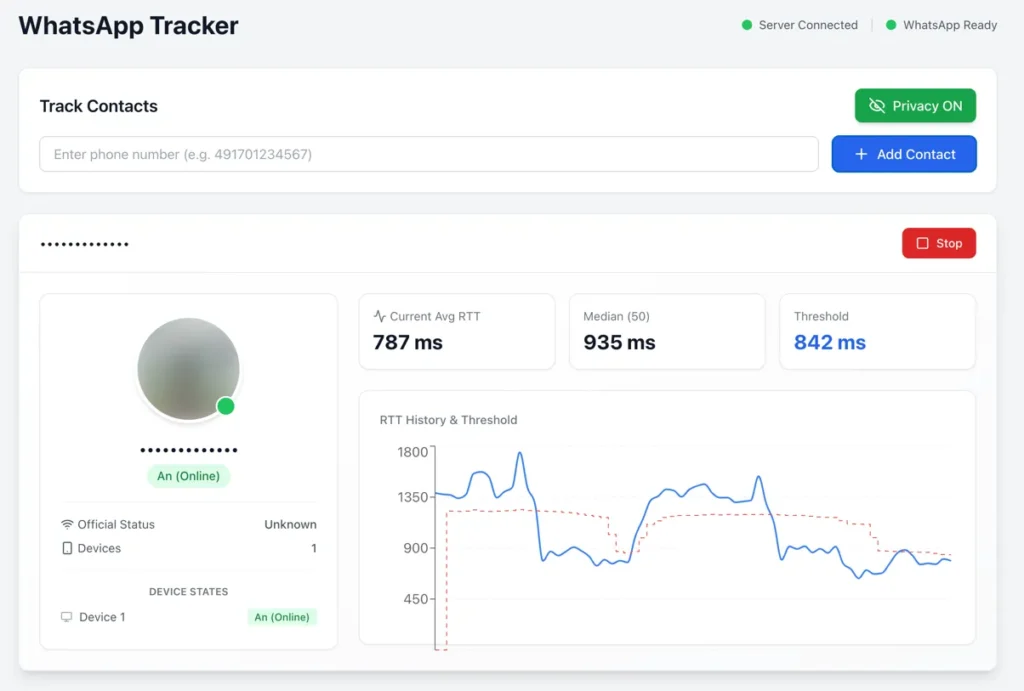
Web Interface (Recommended)
# Terminal 1: Start backend npm run start:server # Terminal 2: Start frontend npm run start:client
Open http://localhost:3000, scan QR code with WhatsApp, then enter phone number to track (e.g., 491701234567).
CLI Interface
npm start
Follow prompts to authenticate and enter target number.
Example Output:
╔════════════════════════════════════════════════════════════════╗
║ 🟡 Device Status Update - 09:41:51 ║
╠════════════════════════════════════════════════════════════════╣
║ JID: ***********@lid ║
║ Status: Standby ║
║ RTT: 1104ms ║
║ Avg (3): 1161ms ║
║ Median: 1195ms ║
║ Threshold: 1075ms ║
╚════════════════════════════════════════════════════════════════╝
- 🟢 Online: Device is actively being used (RTT below threshold)
- 🟡 Standby: Device is idle/locked (RTT above threshold)
- 🔴 Offline: Device is offline or unreachable (no CLIENT ACK received)
How It Works
The tracker sends reaction messages to non-existent message IDs, which triggers no notifications at the target. The time between sending the probe message and receiving the CLIENT ACK (Status 3) is measured as RTT. Device state is detected using a dynamic threshold calculated as 90% of the median RTT: values below the threshold indicate active usage, values above indicate standby mode. Measurements are stored in a history and the median is continuously updated to adapt to different network conditions.
Common Issues
- Not Connecting to WhatsApp: Delete the
auth_info_baileys/folder and re-scan the QR code.
How to Protect Yourself
The most effective mitigation is to enable “Block unknown account messages” in WhatsApp under Settings → Privacy → Advanced.
This setting may reduce an attacker’s ability to spam probe reactions from unknown numbers, because WhatsApp blocks high-volume messages from unknown accounts. However, WhatsApp does not disclose what “high volume” means, so this does not fully prevent an attacker from sending a significant number of probe reactions before rate-limiting kicks in.
Disabling read receipts helps with regular messages but does not protect against this specific attack. As of December 2025, this vulnerability remains exploitable in WhatsApp and Signal.







